With FirePower on ASA, you were able to run next gen firewalling, Anti-Malware Protection (AMP) for networks and next gen IPS on your existing ASA platform, which was awesome. And to be honest, also much easier to manage/operate then Cisco’s own next gen firewall module called ASA-CX.
How is Firepower on ASA operating?
The below schematic is a flow chart on how the ASA (image courtesy of Cisco Live presentations) is handling flows and packets through the firewall.
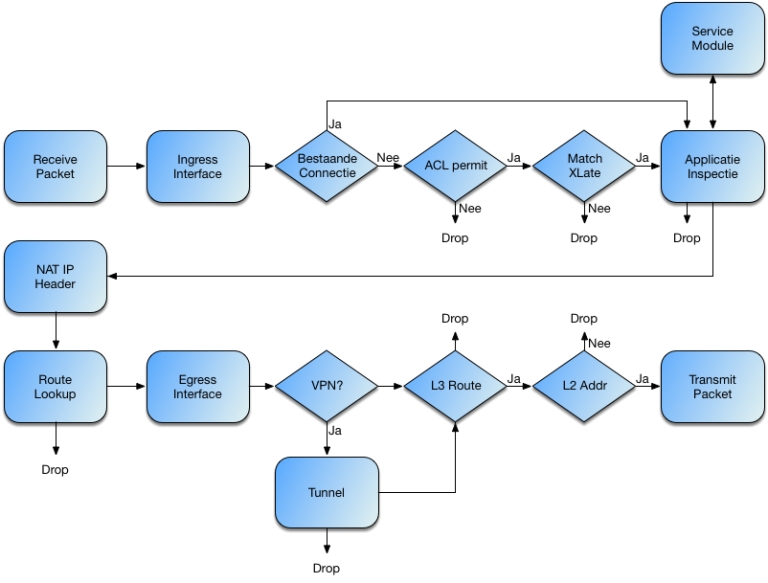
FirePower on ASA is in essence the service module in the diagram. Based on your class-map, the packet is either copied or redirected to the service-module where the FirePower software is doing its part. If a packet needs to be dropped, FirePower informs the ASA that the packet is to be dropped. The two modules run independently and need to be configured and managed by two separate management environments.
FXOS & FTD
Cisco introduced the security everywhere paradigm, including the introduction of the FirePower appliances and a new Security Services Architecture. Those FirePower appliances run a special operating system that you can compare with a hypervisor for virtualization called FXOS. Within FXOS you can configure applications and so-called decorators and configure which interface is linked to which interface and if a decorator needs to be placed inside that application or not. Of course the ASA software is one of these applications, but also a newly introduced application called FirePower Threat Defense, or FTD for short.
The diagram below is an architectural schematic on how FXOS, FTD and decorators can work together in the Security Services Architecture. The number of available security modules is dependent of the FirePower Appliance platform or ASA platform.
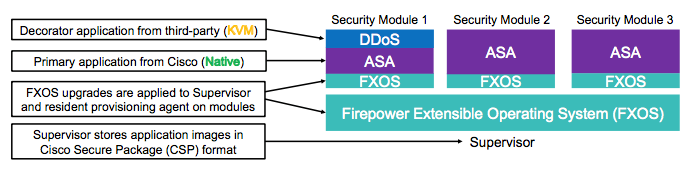
FTD is in essence the unification of FirePower features like NextGen Firewall, AMP, Identity Based Access, IPS and unique key features of the ASA software platform like IPSEC VPN, Security Group Tagging (SGT), QoS and some other stuff.
The schema’s below is a schematical diagram of which features come from which originating platform.
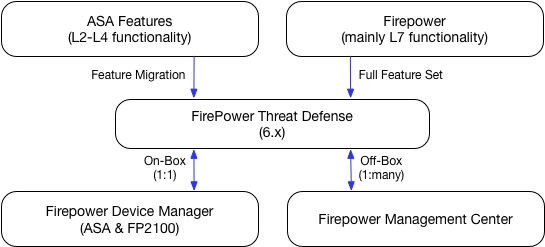
As can be seen in the schema, FTD can only be managed by a FirePower Management Center or FirePower Device Manager (successor of ASDM).There is no real CLI for you to configure FTD, it has to be done via the manager. You have to remember this.
When you run FTD on an FXOS environment, the flow a packet traverses through the firewall is slightly different from the ASA. The diagrams below represent how SourceFire (Snort) and ASA features work together and how a packet traverses inside the FTD instance.
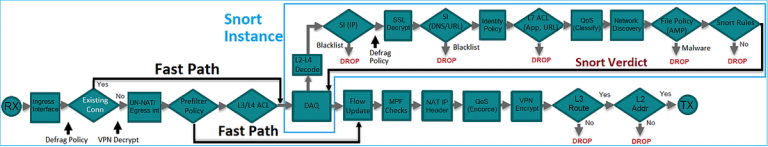
And as can be seen now, the ASA features are actually a service module inside the FTD environment! So the roles have been reversed but with the advantage of having a single management tool that configures all features. And that is a huge advantage, because with FMC you can create a single security policy to be deployed over multiple firepower enabled appliances/modules and have a single pane of view over these devices and connections.
So FTD in essence will be the next major firewall environment for Cisco and with this release Cisco has taken a huge step for those enterprises that use the ASA platform for their versatility. Time to get started on upgrading my environment and get some field experience on FTD 6.2.2..
Info from https://www.nefkens.net/firepower-on-asa-firepower-threat-defense-difference/
More Related:
The Most Common NGFW Deployment Scenarios
Difference between Cisco ASA-FTD and FirePower
What Cisco Platforms Run FTD (Cisco Firepower Threat Defense)? And Advantages of Cisco FTD



















































































































